Is it the End for Virtual Private Networks?
A novel attack on the DHCP server may be the end for Virtual Private Networks (or a new beginning), as virtually any Windows VPN can be attacked by diverting traffic through the DHCP server. Most VPN's use a CIDR /0, however using a rogue DHCP server and multiple /1 routes, traffic can be forced out of the VPN tunnel, while the control channels continue to show the VPN as secure.
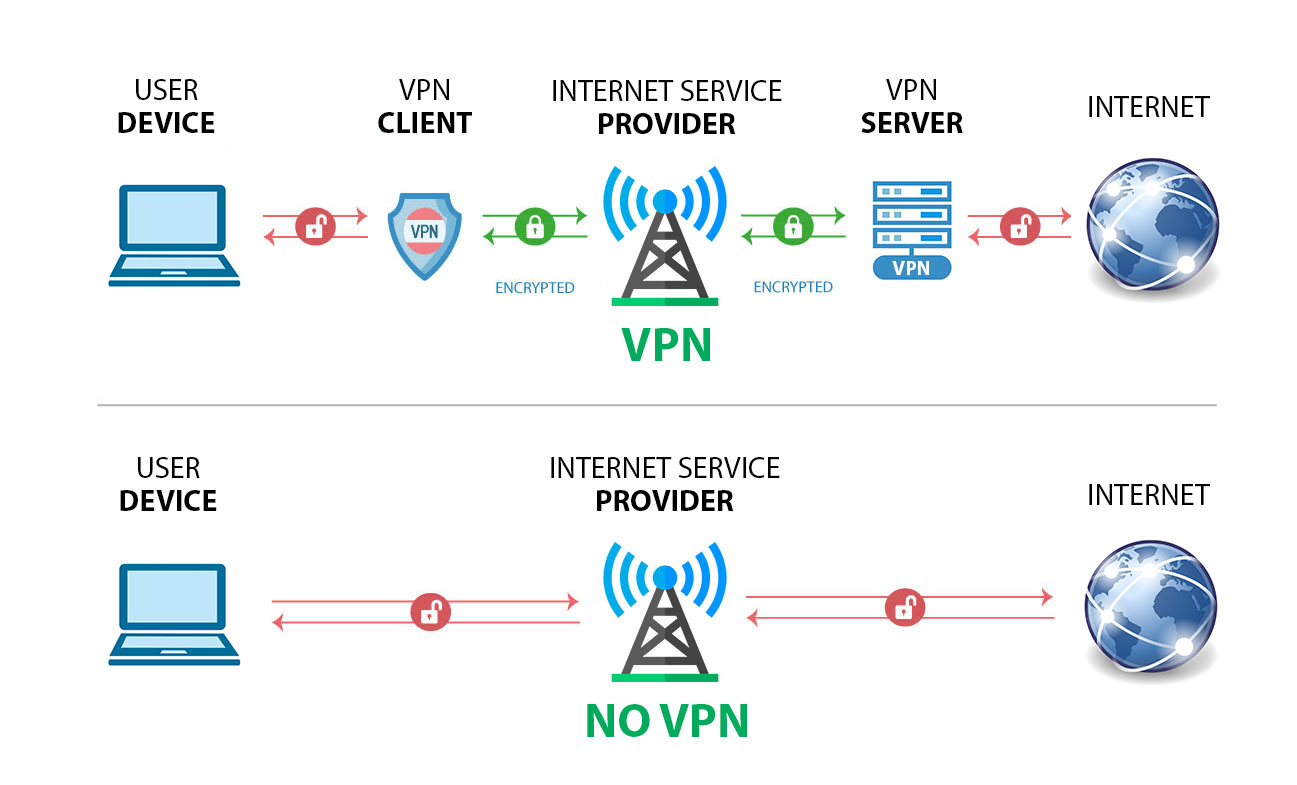 It's called DHCP option 121 and Android is the only operating system that doesn't implement the protocol, so it's currently the only guaranteed VPN platform. Linux mitigates the problem, but may still allow side-channel attacks. Network firewall rules have similar side-channel issues.
It's called DHCP option 121 and Android is the only operating system that doesn't implement the protocol, so it's currently the only guaranteed VPN platform. Linux mitigates the problem, but may still allow side-channel attacks. Network firewall rules have similar side-channel issues.
The attack has been named, TunnelVision, and it takes advantage of a bridged network interface. VPN's bridge the remote network with the local network to allow authorized users remote access.
What this means is that it may be possible to mitigate the vulnerability by running the VPN on a virtual machine whose interface isn't set to bridge, at least that's what Ars Technica advises, but I'm skeptical about that solution, because although the VM's network interface is virtual, it's implementation is through a device's physical ethernet interface.
Learn more at Ars Technica, with Dan Goodin's great coverage.
Estimates suggest there are at least 1.5 billion VPN users globally, so this vulnerability threatens the world's most secure applications.

 It's called DHCP option 121 and Android is the only operating system that doesn't implement the protocol, so it's currently the only guaranteed VPN platform. Linux mitigates the problem, but may still allow side-channel attacks. Network firewall rules have similar side-channel issues.
It's called DHCP option 121 and Android is the only operating system that doesn't implement the protocol, so it's currently the only guaranteed VPN platform. Linux mitigates the problem, but may still allow side-channel attacks. Network firewall rules have similar side-channel issues. 
 What if you could subvert Microsoft Outlook by sending a carefully-crafted e-mail? That's what Microsoft patched today (3/15/2023). You don't even have to open the e-mail for the corrupt code to execute. All you have to do is open Outlook, or potentially Mail. There are several other critical vulnerabilities that Tuesday's patches remediate. Please make sure your Windows operating system is up-to-date with all current patches.
What if you could subvert Microsoft Outlook by sending a carefully-crafted e-mail? That's what Microsoft patched today (3/15/2023). You don't even have to open the e-mail for the corrupt code to execute. All you have to do is open Outlook, or potentially Mail. There are several other critical vulnerabilities that Tuesday's patches remediate. Please make sure your Windows operating system is up-to-date with all current patches. Is your ESXI patched? 2/7/2023
Is your ESXI patched? 2/7/2023 Did you leave Twitter? Did you migrate to the Mastodon commons? It looks a lot like Twitter, but it's a distributed network that isn't collecting your data or marketing products. It's not a company, it's a non-profit, open source, federated social media service. Will Mastodon be able to welcome former tweeters and can admins change the "toot" button to "bellow?"
Did you leave Twitter? Did you migrate to the Mastodon commons? It looks a lot like Twitter, but it's a distributed network that isn't collecting your data or marketing products. It's not a company, it's a non-profit, open source, federated social media service. Will Mastodon be able to welcome former tweeters and can admins change the "toot" button to "bellow?" The Limits of Privacy on Apple Devices
The Limits of Privacy on Apple Devices